iPhone OS, Partitions, Flashing, Hardware, and Reverse Engineering

Apple’s iPhone is known for its tight security, optimized performance, and proprietary hardware/software ecosystem. Unlike Android, iOS is a closed-source operating system, making it difficult for users to modify. However, for technicians, security researchers, and repair specialists, understanding iPhone OS, partitions, flashing methods, hardware, and reverse engineering is essential.
In this article, we’ll break down:
- The iPhone OS (iOS) and its partitions
- Flashing methods for iOS restoration
- iPhone hardware architecture
- Basics of iPhone reverse engineering
1. iPhone OS (iOS) and Its Partitions
Apple’s iOS is based on Darwin (a Unix-like system) and uses an APFS (Apple File System) partition structure. When an iPhone is powered on, it goes through a secure boot process using cryptographic checks to ensure only Apple-signed code runs.
iOS Partition Layout
iPhones have multiple partitions, each serving a critical function:
iPhone Boot Process
- BootROM (Read-Only Memory) → iBoot → Kernel → iOS UI
- Uses Secure Enclave for encryption and authentication.
- Sandboxed apps prevent unauthorized modifications.
2. iPhone Flashing Methods
Flashing an iPhone involves reinstalling or updating iOS firmware. This is required for repairs, unlocking, or fixing corrupted system files.
Flashing Modes in iPhones
Recovery mode
DFU MODE
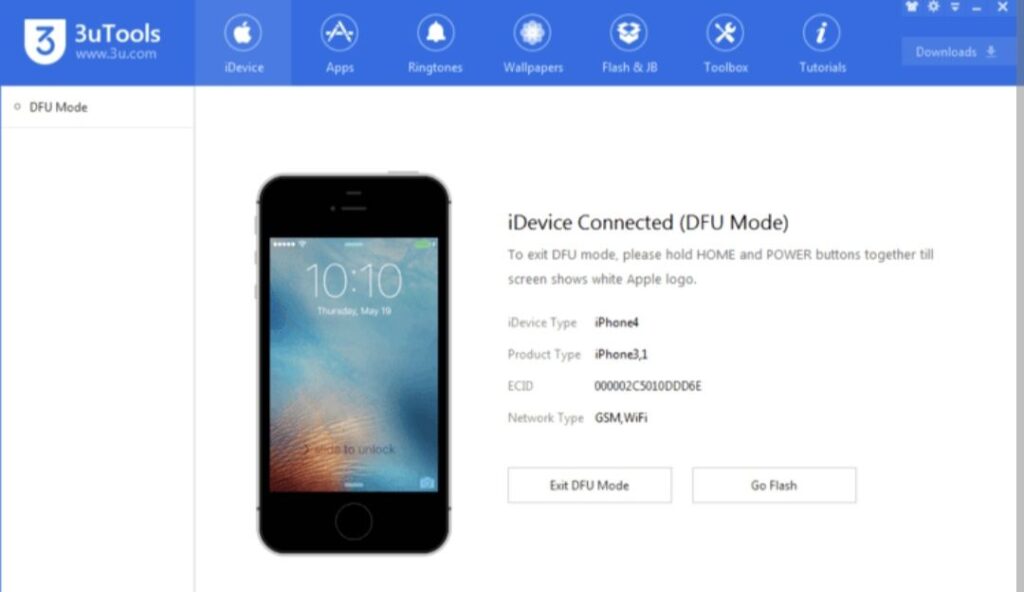
Tools for Flashing iPhones
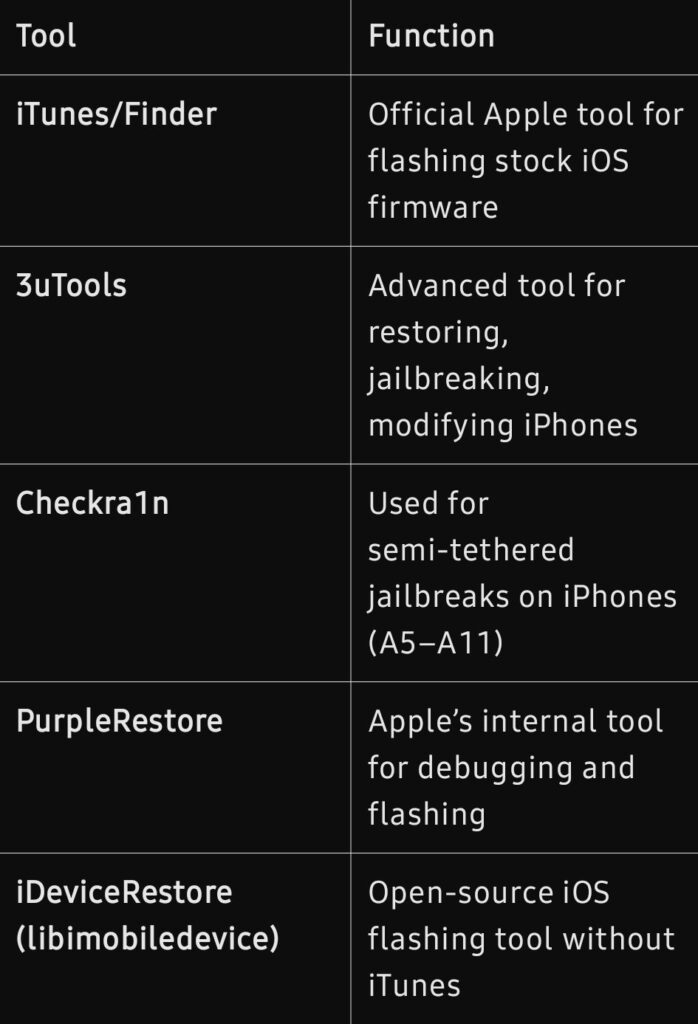
Flashing Process (Using iTunes or 3uTools)
- Download the correct iOS firmware (.ipsw) file.
- Enter Recovery or DFU Mode.
- Open iTunes or 3uTools and select Restore.
- Load the IPSW file and start the flashing process.
- Wait for the iPhone to restart and set it up.
3. iPhone Hardware Architecture
Apple’s hardware is tightly controlled, featuring custom processors, secure boot chips, and proprietary components.
Key Hardware Components
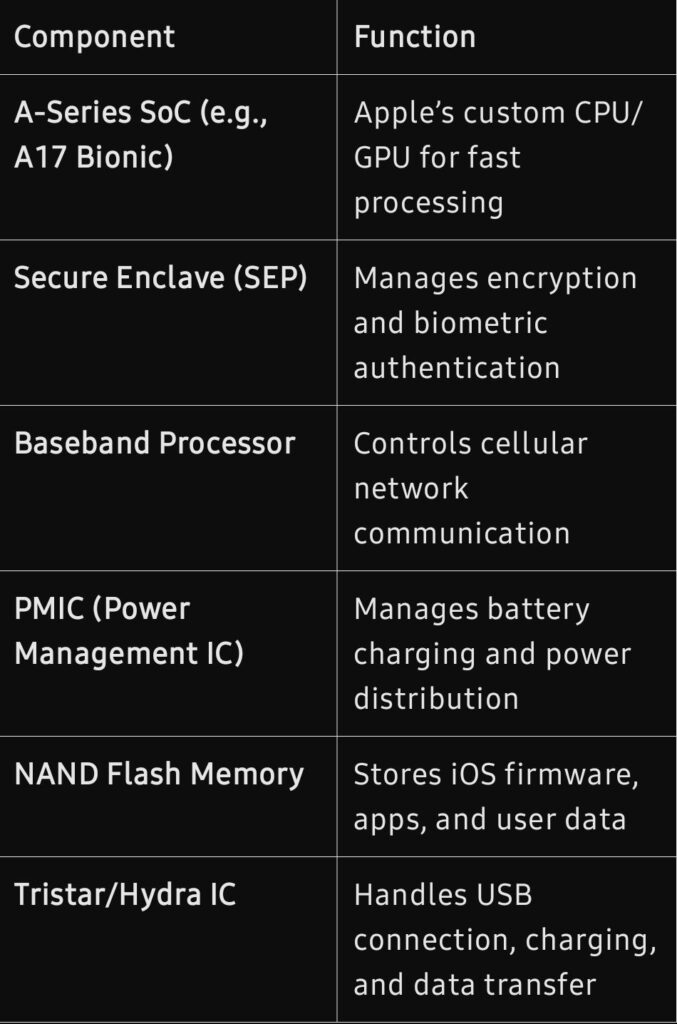
Common Hardware Issues in iPhones
- No power? → Check PMIC, charging IC, and NAND.
- No network? → Baseband or antenna failure.
- Boot loop? → Corrupt firmware, NAND failure, or Tristar IC issues.
- No Face ID? → Damaged TrueDepth camera or SEP failure.
4. iPhone Reverse Engineering
Reverse engineering an iPhone involves analyzing its hardware, software, and security mechanisms. This is used in security research, forensic investigations, and advanced repair techniques.
Reverse Engineering Methods
Checkm8 & iOS Exploits
Checkm8 is a permanent bootROM exploit affecting A5–A11 chip iPhones. It allows:
- Bypassing activation locks.
- Extracting system data for forensic analysis.
- Performing custom firmware modifications.
However, newer chips (A12 and above) have stronger security, making them harder to exploit

iPhone repair and security research require a deep understanding of iOS partitions, flashing techniques, hardware components, and reverse engineering tools. Whether you’re a repair technician, security researcher, or advanced user, knowing these fundamentals can help you diagnose and fix iPhone issues efficiently.
